Press release
AcuteNet Customers Join the AlayaCare Family

Around the world healthcare institutions are modernizing systems to deliver better outcomes for patients. Driving this pursuit is data science – because the more data an organization has, the more trends it can unearth, and the more strategies it can take to deliver precision care.
Data scientists are leveraging emerging technologies, such as machine learning, to not only measure but predict clinical outcomes. Inside our AlayaLabs division, teams are tapping the emergence of AI to strategize and build machine learning models toward this very end.
First, a word on structured and unstructured data
While data science has rapidly advanced, institutions are still very much in the early stages of capturing data consistently and using it wisely. In order to truly advance patient care by using data, one needs a machine learning model that can analyze both the structured and unstructured data that exists within electronic health records (EHRs).
Most models rely on EHR structured data – clinical metrics like cholesterol count, blood pressure levels, a diagnosis, a drug allergy. Those models have a hard time extracting and analyzing unstructured data such as progress notes. But by missing these details, a patient’s overall health status isn’t accurate – the clinical data is not as robust as it needs to be, and errors can happen as important data can be buried in notes and not in the proper boxes on forms.
While AlayaCare explores clinical data and confronts these challenges, we have some exciting new opportunities ahead after a valuable new acquisition.
InterRAI assessment data and its potential
In March 2021, AlayaCare acquired AcuteNet, an Ontario-based company that specializes in interRAI and enables flexible clinical assessments.
InterRAI is a widely adopted system that standardizes the approach and language used by healthcare providers across hospital, home and community settings. InterRAI assessments provide a valuable source of information as they can be applied to patient care plans to better track patient health and care services.
This protected health information, private and secure, elevates the AlayaLabs team from a clinical perspective – by helping define questions in need of answers. Analyzing RAI data can help decode, for example, what care services are most important to patient outcomes, the impact of when care is delivered, and where to align resources and budgets in the areas of greatest benefit.
More clinical AlayaLabs AI projects underway
Our pursuit of clinical data has opened new doors with partners such as CareMaster, a U.S. home care agency with thousands of clients. For them, the AlayaLabs team has begun a pilot to leverage unstructured clinical data such as visit notes and ADLs to flag incidents that fall outside structured forms.
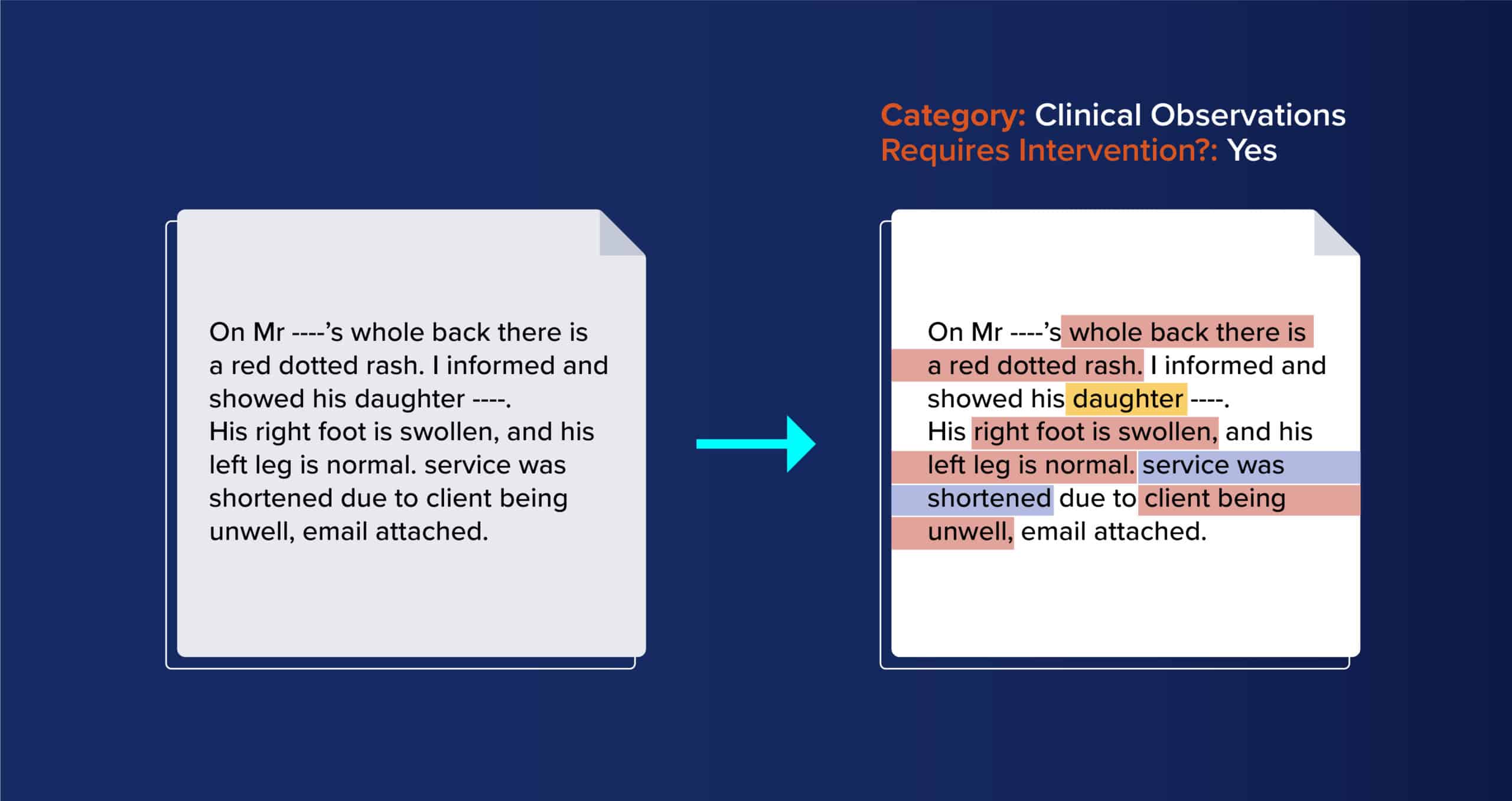
For example, using NLP (natural language processing) techniques, raw text can be transformed into actionable, usable facts and insights. Take these two notes for example. On the left, a typical note. On the right, that same note with issues automatically flagged to indicate where intervention is required:
In such pilots, AlayaCare is confronting the challenge of how to use unstructured clinical data to influence outcomes. The potential to build upon the risk of hospitalization model – a huge KPI for home care agencies – is vast: using assessment data, care plan progress data, vital, self-assessments and more.
For the possibilities within clinical data, we sit at the tip of the proverbial iceberg when it comes to enabling organizations to achieve more efficient operations and deliver top quality care. Through AI initiatives, we can help agencies generate new service opportunities as we continue our partnerships today and into the future.